Users
Menu name change
In the Admin console, the Users menu has been renamed to Users & Permissions. This change more accurately reflects the options that are available in this menu.
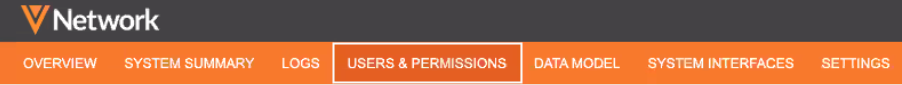
Field restrictions
Administrators can now apply field-level access for specific users or user groups. Previously, field access could only be managed using profile layouts. Now, you can set read-only or edit permissions on specific restricted fields.
This feature is available by default.
Permissions
To grant access to a restricted field, you can assign permissions to specific users and user groups for applicable countries. User groups can be created to efficiently manage field access. Previously, user groups were available to use for restricting access to custom objects through dynamic access control. They can now be used for field restrictions.
The following permissions can be assigned to users and user groups:
- Read-only - Users can view the field and value but cannot edit the field. A lock
 icon displays when you hover over the field value on the record profile.
icon displays when you hover over the field value on the record profile. - Edit - Users can view and edit the field value.
When a restriction is applied to a field, it becomes hidden to all other users in your Network instance and through the API. For example, if you create a restriction on the field gender__v , all users have no access to the field in your Network instance and in the API.
Field restriction exceptions
Restricted field access is not applied to the following features:
- Data change requests (DCRs) - Data stewards and data managers can see the field and value on DCRs. If the request is approved, the field will be hidden from them in the rest of the Network UI if they do not have view or edit permission.
- Data load - Restricted fields can be loaded into your Network instance using source subscriptions and data updater. All updates are logged and can be viewed in the Revision History.
- Target export - Restricted fields are available in target subscriptions so you can filter them from the export.
Fields that cannot be restricted
Most standard and custom fields can be restricted. The fields that are not supported are system fields and fields that are used for key Network processes.
Fields that cannot be restricted:
- System fields - Veeva standard fields that are created when a record is created (
created_date__v,record_status__v,vid__vand so on). - Required data model fields
- Custom key fields
- Candidate record field (
candidate_record__v) - Disabled fields
- Cluster Management fields
Create a field restriction
- In the admin console, click Users & Permissions > Field Restrictions.
-
Click Add Field Restriction.
The Create Field Restriction page displays.
-
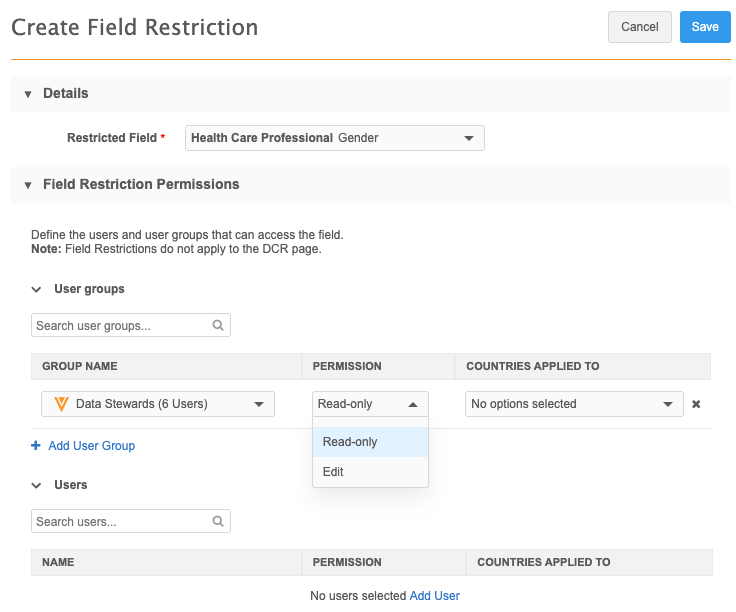
In the Details section, select the field from the Restricted Field list.
Sets of fields display as their grouped name instead of the individual field name. For example,
All Emailsdisplays instead ofemail_1__v,email_2__vand so on. -
In the Field Restriction Permissions section, identify the permissions for user groups and individual users.
- Name - Select the group or user from the list.
- Permission - Choose Read Only or Can Edit
- Countries applied to - Select the countries for each group and user permission. The list is filtered to include only the countries that the field is enabled for.
- Save your changes.
The field restriction is now active. Only the users that have Read Only or Edit permission can access the field.
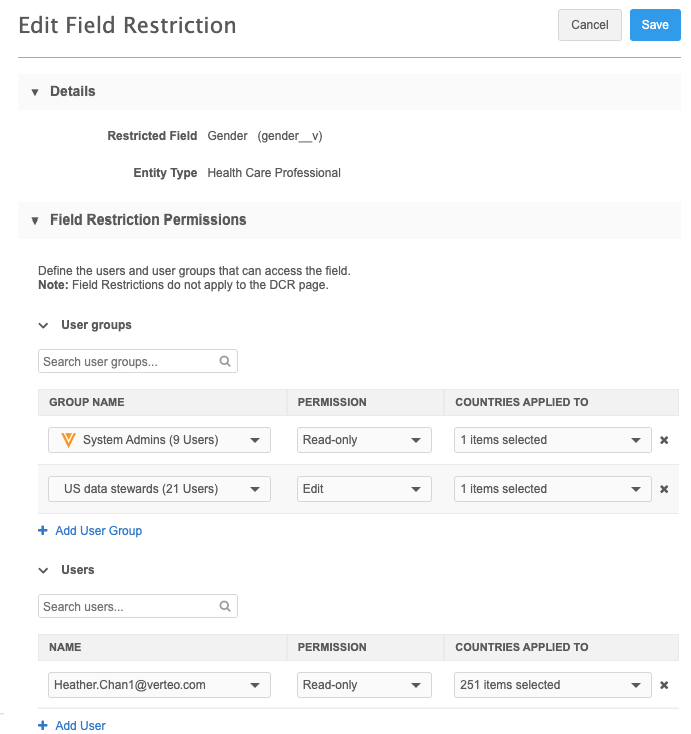
View all field restrictions
All of the field restrictions in your Network instance are listed on the Field Restrictions page. The restrictions are sorted by the Field Label column.
Clone field restrictions
Cloning an existing restriction can save time if it applies to the same users and countries.
To clone a restriction
- On the Field restriction page, click Clone.
-
In the Clone dialog, choose the new field and click Next.
The field restriction is immediately created with the permissions and countries applied for the users.
- Add or change any user group or user permissions.
-
Click Save to update the restriction.
If you click Cancel, the field restriction is saved without any changes that you made.
To remove the cloned restriction, click Remove Restriction.
Delete field restrictions
When field restrictions are deleted, the field becomes accessible to all users.
- To delete a restriction, click the Delete
 icon.
icon.
User page
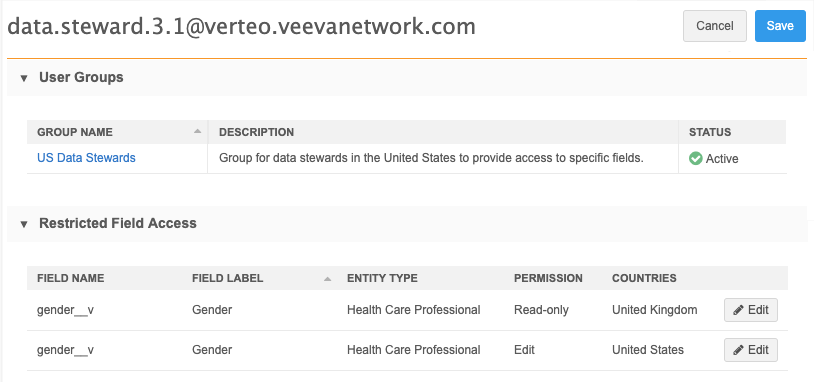
To support this new feature, the User page is updated to include a section called Restricted Field Access. This section displays all of the restricted fields assigned to the user. Each row displays the field name, entity type, permission, and country that the permission applies to. If the user has different permissions for the same field for different countries, the field displays on separate rows.
The field restriction can be edited from the User page.
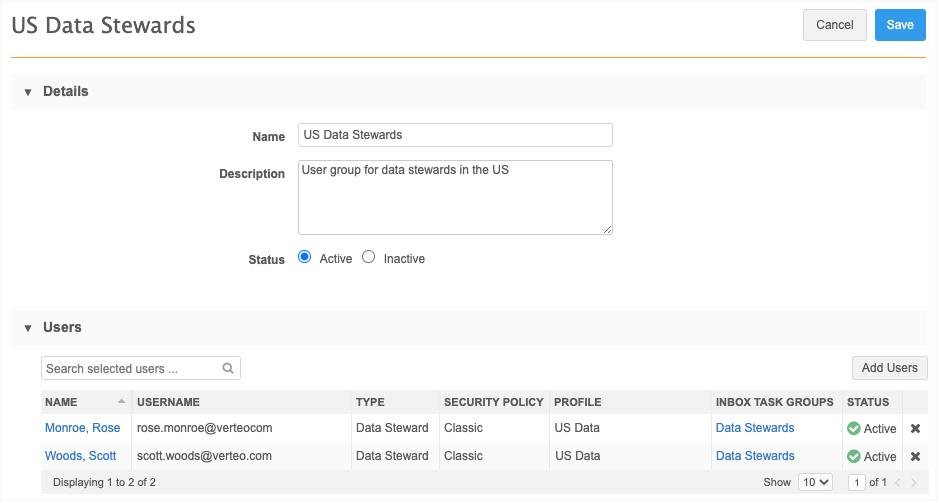
User Groups
Previously, user groups were available to assign permissions to specific custom objects using the Dynamic Access Control feature. User groups can now be used for field restrictions so you can quickly assign and update permissions to groups instead of individuals.
For more information, see User groups in the Veeva Network Online Help.
Data model
In the data model, administrators and data managers can use a new column, Field Access, to quickly see what fields are available to all users or are restricted.
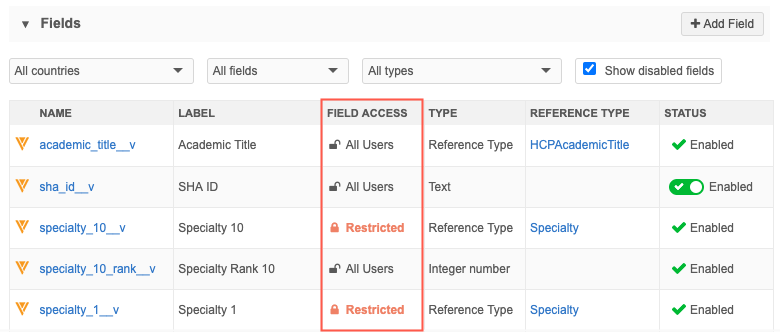
- Click the Restricted link to navigate to the field restriction for more information or to make changes (administrators only).
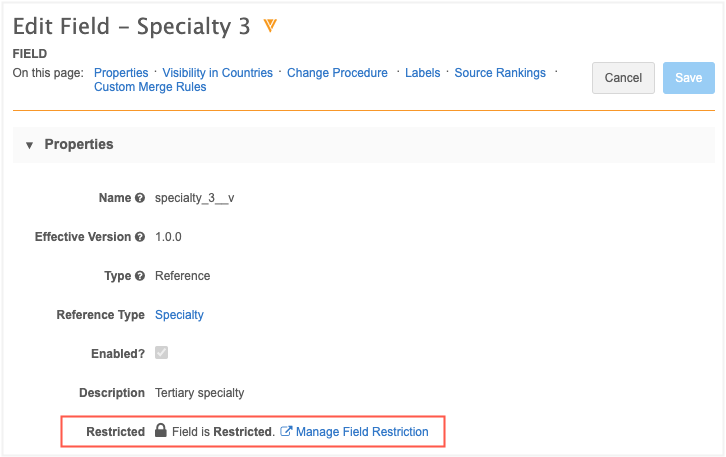
- Click the field name to open the configuration page. The Properties section shows that the field is restricted. Administrators can click the Manage Field Restriction link to navigate to the Field Restrictions page for more information.
Required fields
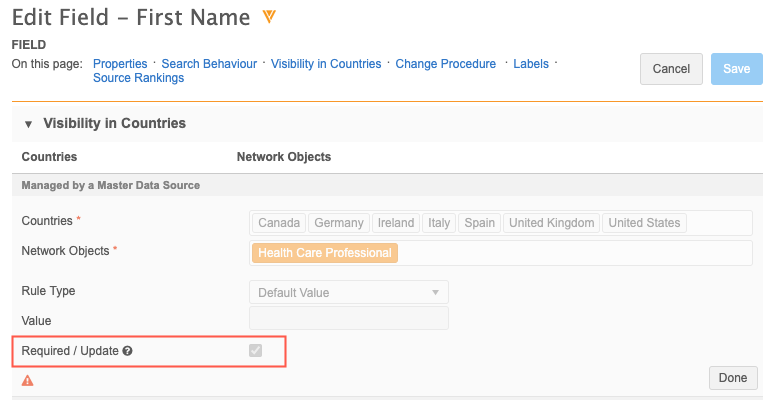
If a field is set as Required/Update, field restrictions cannot be applied to it because all users must be able to view it. Similarly, if field restrictions have been set on a field, the Required/Update option is dimmed and cannot be selected.
To see if a field is required, open the field's configuration page from the data domain. In the Visibility in Countries section, select a country group and view the Required/Update option.
Report considerations
If you run a report, the results will return the field column but the value will be empty.
Network API
Restricted fields are hidden from Integration users in the response for the following API calls:
- Search
- Retrieve Entities
- Retrieve Change Request
- Batch Retrieve Change Request
Logs
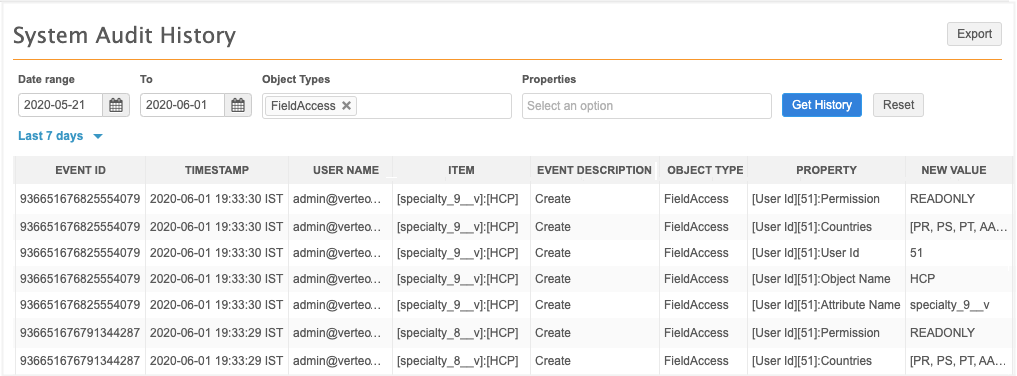
Administrators can track new restrictions and changes to existing restrictions in the System Audit Log. In the Object Type field, select FieldAccess to view all of the field restriction actions in your Network instance.
Configuration management
Field restrictions cannot be exported to a target environment because the users on the target might be different.
API access permissions
Administrations can now define the specific systems that users with API permissions can access. Previously, users were either allowed all access or no access to the Network API. Linking the user to the system prevents users from performing API calls under an incorrect Network system. For example, if you have an Integration user for a portal, you can give the user access to only the portal system to ensure they don't accidentally make API calls for another system.
This enhancement is available by default in your Network instance.
Define API access
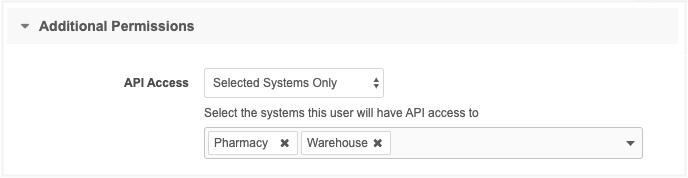
To define API access for a user, go to the Additional Permissions section on the user profile.
The API Access list now contains three options:
- Don't Allow - Users do not have access to the Network API
- Allow All Systems - Users have access to perform API calls from all systems.
-
Selected Systems Only - Users have access to perform API calls from the defined systems.
If you choose this option, identify the systems using the list.
When the permission is applied, if users try to make API calls from a system that they do not have access to, an error occurs.
Updates to API calls
To support this feature, API calls that are used to change data will enforce systems permissions.
The following API calls are affected:
| Change Request | Associate Custom Key | Create and Cancel Subscription Jobs |
|---|---|---|
| Create Change Request | Associate Custom Keys | Create Source Subscription Job |
| Update Change Request | Batch Associate Custom Keys | Cancel Source Subscription Job |
| Create Change Request | Associate Custom Keys to Children | Create Target Subscription Job |
| Batch Associate Custom Keys to Children | Cancel Target Subscription Job | |
| HCP Associate Key (4) | ||
| HCO Associate Key (4) |