Dynamic access control
Administrators can provide more granular access to custom objects by using rules that are assigned to specific users. Dynamic access control can be enabled on individual custom object in your Network instance. When it is enabled, access to the object is permitted only through the rules to the defined users. Users must also have access to the object through their data visibility profiles.
Dynamic access control can be used for custom objects that are enabled in your Network instance. It can be disabled on the custom object after it has been enabled.
How it works
Dynamic access control works with data visibility profiles (DVPs) to provide access to individual custom objects.
When dynamic access control is enabled for a custom object, no user can access object records until rules are created and assigned to user groups or individual users. If the rule conditions are met and users have access to the custom object through their data visibility profile, they will have access to the custom object records that meet the rule criteria. For custom objects, DVP access is either all access or no access.
When dynamic access control is not enabled, permissions to access to custom objects is defined only through a user's data visibility profile permissions. This is the existing behavior that has always determined access to custom objects.
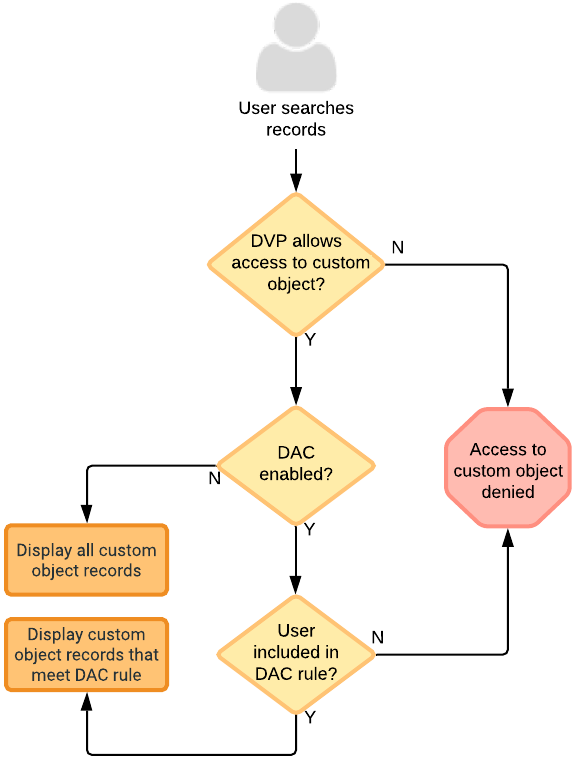
When dynamic access control is enabled, users must belong to a rule and have data visibility permissions to access the custom object records.
Users with access to the restricted custom object can do the following:
- Search for records
- View the records on the profile page
- View record relationships from Network Explorer
- View data change requests (DCRs)
- See the records in their inbox
- Retrieve record information using ad hoc queries (reporting)
- Access records using the Network API
All other users will have no access to the custom object.
Access to restricted custom objects through relationships
Before enabling dynamic access control on a custom object, consider the object's relationship to other objects. On the Profile page, relationships to restricted custom objects will be hidden for users that don’t have access. However, restricted data could be exposed to unauthorized users through the relationship object on the Revision History or Data Lineage pages if dynamic access control is enabled on a Related object: all relationship objects have an Owner and Related object.
Examples
Review the examples for the Study and Patient custom objects to understand how you can restrict relationship data.

Example 1 – Dynamic access control is enabled on the Owner object
In this scenario, you have access to Patient records. Dynamic access control is enabled on the Study custom object (Owner object) and you do not have access to Study records. In this case, when you are viewing Patient records, you cannot see any relationships to Study records.
Example 2 – Dynamic access control is enabled on the Related object
In the opposite scenario, dynamic access control is enabled on the Patient custom object (Related object). You do not have access to Patient records, but you have access Study records. In this case, when you are viewing the Revision History and Data Lineage for a Study record, you will be able to see Patient record information because relationship data is governed by the Owner object (Study).
To prevent users from being able to view restricted record data, consider using dynamic access control on the Owner object.
Enable dynamic access control
Dynamic access control can be applied to enabled custom objects only. Custom sub-objects and relationship objects inherit the permissions assigned to the related object.
To enable dynamic access control for a custom object:
- In the Admin console, click Data Model and choose the data domain for the custom object.
- Select the custom object from the list.
-
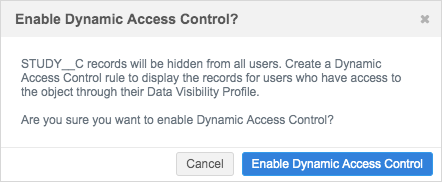
In the Dynamic Access Control section, click Enable Dynamic Access Control Rules.
This section is dimmed if the custom object is not enabled.
- In the dialog box, click Enable Dynamic Access Control.
Next steps
After dynamic access control is enabled, no users have access to the custom object records until you create rules and add users or user groups.
- Create rules - Define the rules that will provide users access to the custom object.
- Create user groups - Rules can be applied to user groups or individual users. Creating user groups can simplify your user permission assignments.
Considerations for Network features
User access
There are some Network features where users will see the object data masked or a locked profile page if they don't have access to the custom object.
- My Requests - Users that do not have access to a custom object can still create an add request for the object. After the data change request is sent, their My Requests page displays the request but the record cannot be accessed. Clicking the request displays the locked page.
-
Inbox - Data stewards that do not have access to a custom object can view tasks in their inbox if they belong to an inbox task group that has access to the custom object. The data in Entity column is masked with "Inadequate Access Permission". Clicking the task opens the locked page.
Values in columns are not populated for restricted objects.
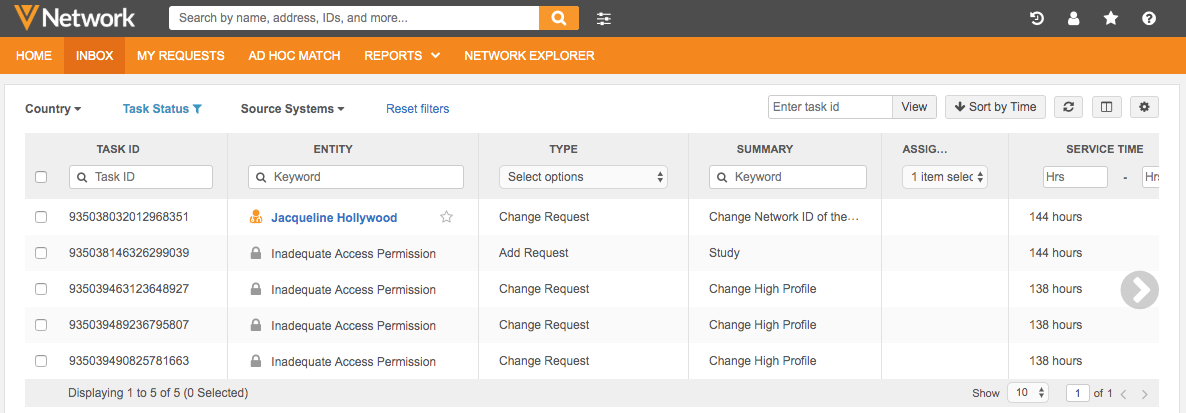
To prevent these tasks from displaying for these data stewards, consider creating an inbox task group specifically for users with access to the custom object.
- Reports - Users that do not have access to custom objects can run reports that include the custom object but the report results will not return records that the user does not have access to through dynamic access control.
- Recent items - If users previously had access to a custom object and their permissions changed, the Recent list still contains the record name but the record cannot be accessed. Clicking the recent item displays the locked page.
Network Explorer
If users do not have access to a custom object, Network Explorer hides the relationships to objects; they do not display on the canvas.
Target subscriptions
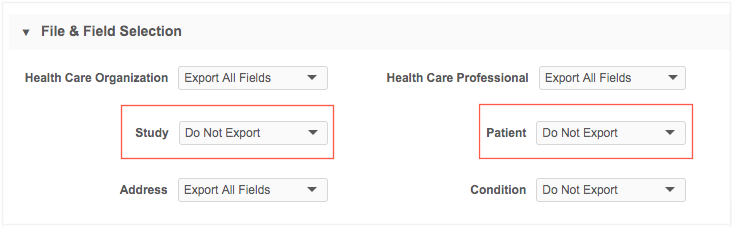
To prevent restricted custom objects from being exported to downstream systems, administrators can filter the custom object in the target subscription.
In the File & Field Selection section, ensure that Do Not Export is selected for any restricted custom objects that should not be included in the export.
Logs
The System Audit History tracks any changes to dynamic access control configurations.
Network API
If the Network integration user does not have access to records through dynamic access control, the following behavior occurs:
- Search API - Restricted records are not returned.
- Retrieve DCR API - Data change request details are masked with "Inadequate Access Permission".
{
"responseStatus": "SUCCESS",
"change_requests": [
{
"change_request_id": "935039860349272479",
"status__v": "CHANGE_PROCESSED",
"result__v": "CHANGE_ACCEPTED",
"entity_type": "PATIENT__C",
"vid_key": "Network:Entity:935038590152671615",
"vid__v": "935038590152671615",
"metadata": {
"creator": "jessie.steward@verteodev.vdmdev.com",
"note": "",
"source": "Entity Profile Editor",
"system": null
},
"resolution_notes": [
{
"comment": "System approved - Created by data steward.",
"fields": [
"address_line_1__v",
"address_status__v",
"address_type__v",
"administrative_area__v",
"country__v",
"locality__v",
"address_line_3__v",
"address_line_2__v",
"postal_code__v"
],
"created_date": "2019-08-22T02:47:22.116Z",
"code": "A-00011"
}
],
"entity": {
"addresses__v": [
{
"vid_key": null,
"vid__v": "935039860390494592",
"object_id": "935039860307657120",
"address_line_1__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"address_status__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"address_type__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"administrative_area__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"country__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"locality__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"address_line_3__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"address_line_2__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
},
"postal_code__v": {
"change_requested": "Inadequate Access Permission",
"final_value": null,
"result": null
}
}
]
},
"created_date": "2019-08-22T02:47:22.000Z",
"completed_date": "2019-08-22T02:47:23.000Z",
"taskCountry": "US",
"task_type": "CHANGE_REQUEST",
"original_task_type": "CHANGE_REQUEST",
"parent_task_ids": [],
"reserved_vid": null
}
]
}
Disable dynamic access control
If you disable access control, the custom object becomes visible to all users that have access to the object through their data visibility profiles.
All active rules on the custom object will be disabled. Administrators cannot create new rules for the custom object from the Dynamic Access Control summary page (Users & Permissions > Dynamic Access Control).