Security
IP access control
To help block unauthorized access, Administrators can create rules that define the IP ranges that can access Network based on user security policies.
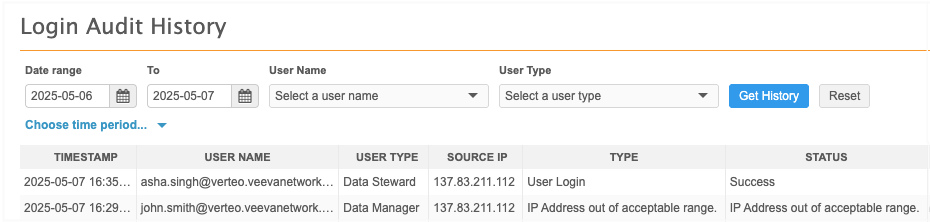
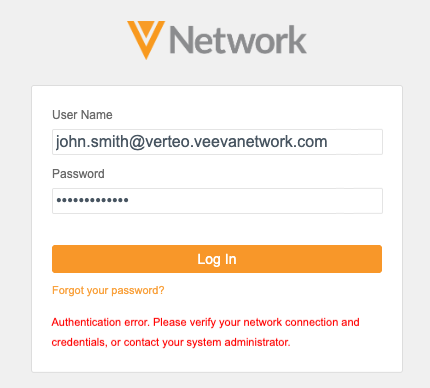
Users that log in outside of the defined IP range receive an error. After five unsuccessful login attempts, the user is locked out of Network.
This feature is available by default. Administrators must configure the rules.
Note: This is an optional feature. If IP Access Control rules are not created, there is no impact for users logging into your Network instance.
Supported users
IP Access Control rules are assigned to a security policy. Users assigned to the security policy must log into Network within the IP range.
IP Access Control does not apply to users that authenticate to Network using single sign-on (SSO).
Supported authentication methods
IP Access Control rules apply when users log into Network in the following ways:
-
UI authentication (Network log in page)
-
API authentication
-
FTP access authentication
Prerequisites
-
Create a security policy - IP access control rules are assigned to security policies. Create a policy to define the IP address ranges that are allowed to access your Network instance (Settings > Security).
-
Assign the security policy to users - Assign the policy to users (Users & Permissions > Users).
Create an IP access control rule
Create a rules that allow or restricts access for specific IP address ranges.
Example rule
-
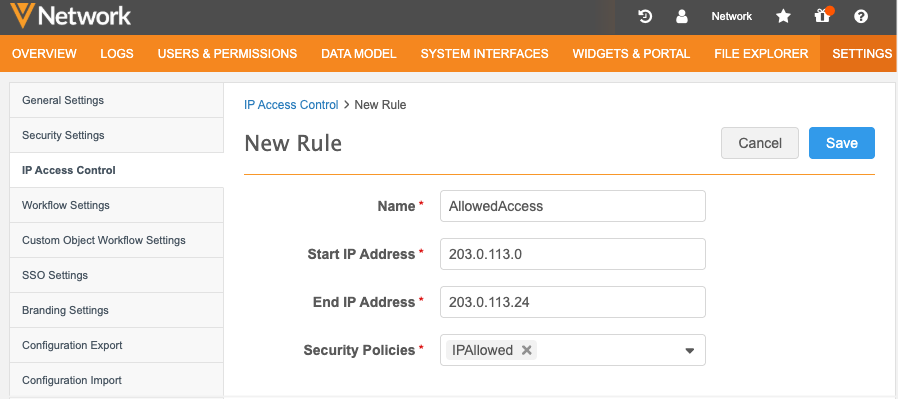
In the Admin console, click Settings > IP Access Control.
-
Click Add Rule.
The New Rule page displays.
-
Name and Description - Type a meaning name and details about the rule.
-
Start IP Address - Type the start of the allowed IP address range.
The IP addresses must be IPv4 address standard, for example: 137.43.211.1114.
-
End IP Address - Type the end IP address in the range.
-
Security Policies - Select the security policies to apply to the rule.
Note: The rule is validated to ensure that the IPs are valid and that you are not creating a rule that locks you out of Network.
-
Save your changes.
User page updates
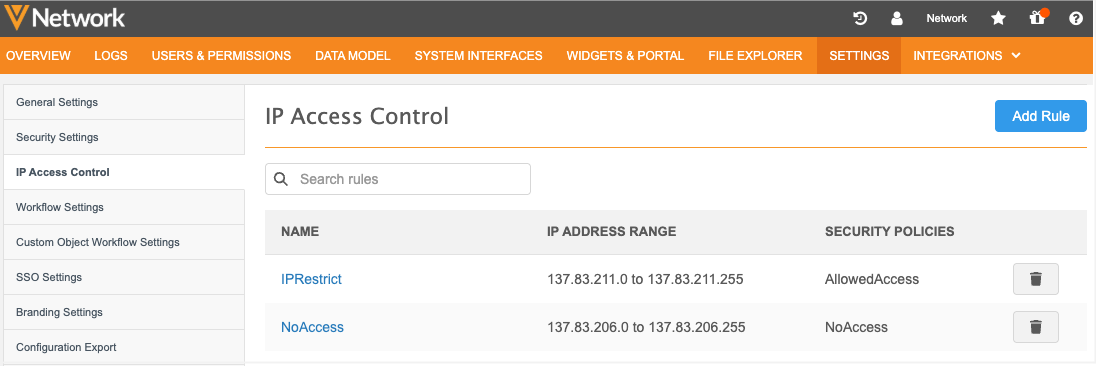
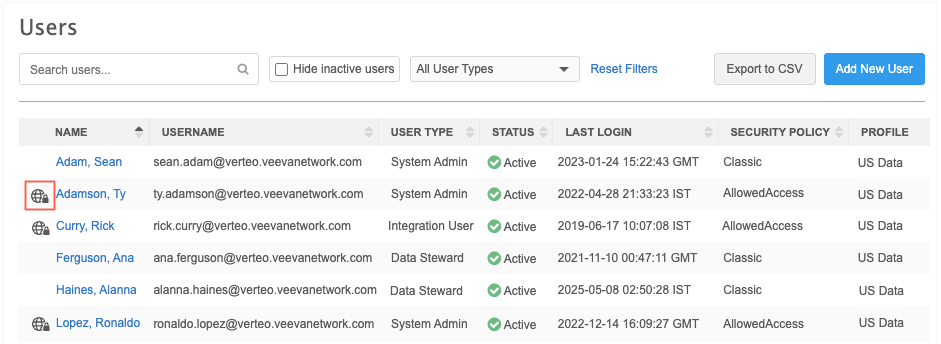
Administrators can quickly identify impacted users from the Users page (Users & Permissions).
An icon displays beside the name of any user where IP access control rule is applied to their assigned security policy.
Logs
Administrators can monitor the Network logs to take appropriate actions.
-
System Audit log- Track changes to IP Access Control range settings.
-
Login Audit Log - Review authentication failures due to IP access control.