About the SAML process
Network supports SSO using Security Assertion Markup Language (SAML) 2.0 for both service provider (SP) initiated and identity provider (IdP) initiated models. For Network, both SSO models use HTTP POST binding.
IdP-Initiated SAML Login Process
The following steps detail how SAML login, using and IdP-initiated login flow, works for Network.
- Admin establishes a trust relationship between the IdP and the SP by providing a certificate to the SP that the IdP has generated. Any communication from the IdP to the SP has to be ‘signed’ with this certificate.
- A user logs into the IdP with her credentials.
- The user selects an application (SP) from a list managed by the IdP.
- The IdP returns a SAML response that is digitally signed by the IdP with its certificate.
- The browser takes the SAML response and posts it to the SP. The SP confirms that the response is properly signed and, if so, gives the user access to the application.

Identity Provider-Initiated SSO example
- Tom arrives at work and logs into his SSO-enabled applications through the identity provider’s portal.
- When he subsequently opens Network, he bypasses the login screen and goes directly to his inbox, because he has already logged in through the identity provider.
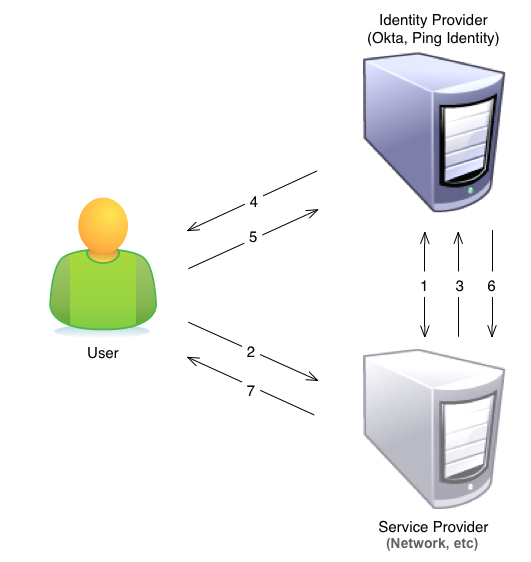
SP-Initiated SAML Login Process
The following diagram and steps detail how SAML login, using and SP-initiated login flow, works for Network.
- Admin establishes a trust relationship between the IdP and the SP by providing a certificate to the SP that the IdP has generated. Any communication from the IdP to the SP has to be ‘signed’ with this certificate.
- The user opens the application (SP) website.
- If the user’s authentication doesn’t exist because she has never logged in or the session has expired, the SP contacts the IdP by sending a SAML AuthnRequest. The following steps apply only if the user is not already authenticated.
- The IdP displays a login window for the user.
- The user logs into the IdP with her credentials.
- The IdP returns a SAML response that is digitally signed by the IdP with its certificate. The browser takes the SAML response and posts it to the SP.
- The SP confirms that the response is properly signed and, if so, gives the user access to the application.
Service Provider-Initiated SSO example
- Tracy arrives at work and opens Network directly.
- From Network, she’s redirected to the identity provider’s login portal.
- She is then redirected back to Network.